The importance of roles in today’s modern enterprise
By John Thornton
What are roles and why do we need them?
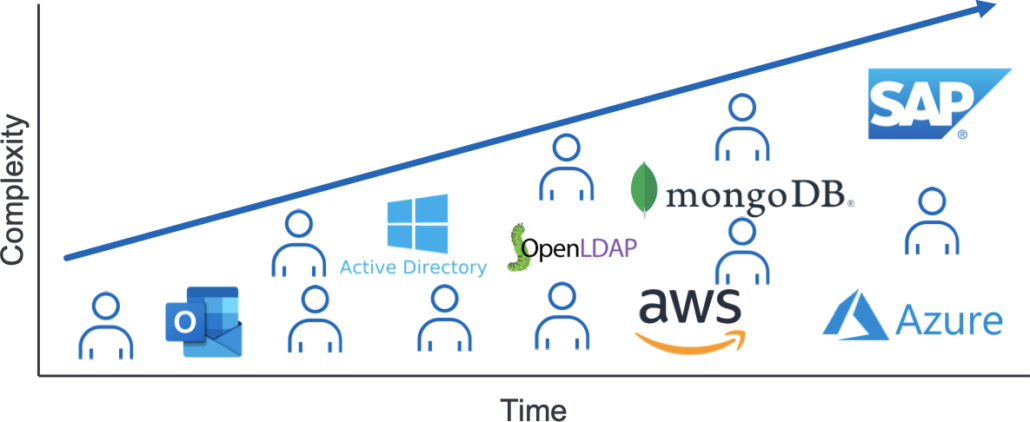
As companies expand and mature the complexity of their access grows along with them. This access complexity is the result of a greater number of people working with a greater number of applications. Access complexity results in a greater workload to onboard or transition employees or lengthier and more error prone access certifications.
Roles Address Access Complexity Growth
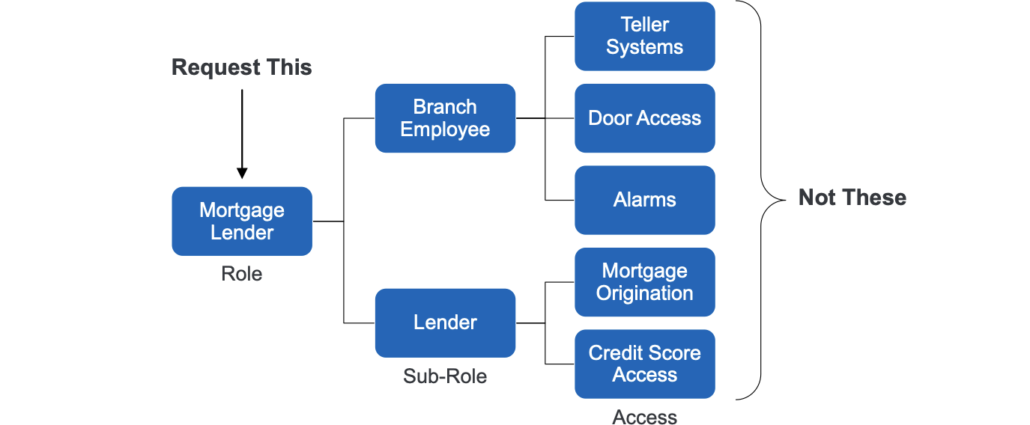
Roles address the growth in access complexity by enabling stakeholders to perform operations such as requesting or reviewing access in a way that’s logically connected to the population the access is being granted to. In the example above, the access that a mortgage lender needs to perform their job is granted to them by way of two sub-roles. Each sub-role encompasses different aspects of their job function as a lender and branch employee, which, in turn, contain all the access needed perform those specific jobs. By using this role for access request and certification the effort to perform either task is reduced five-fold. Instead of working with the entitlements listed on the right, the management team would simply request or certify the role on the left.
How have they been created historically?
In order for roles to be successful at reducing access complexity they must be created properly. The roles need to have the correct entitlements in them and have the correct assignment logic. There are two competing schools of thought on how to do this.

Bottom-up role mining finds role candidates by looking for clusters of common access across the whole of an organization. Each cluster is identified as a role candidate only by its access commonality and requires human intervention in order to assign meaning, such as a job title or an organizational division. It is possible that it will even identify organizational structures within a client that do not exist in your org structure. For example, at a former client of ours we could see the remains of a corporate acquisition spelled out in their entitlement data. The advantage to a bottom-up approach is that it can only produce roles that have a strong correlation with the underlying entitlements allowing the greatest amount of role value to be captured. The disadvantage to the bottom-up approach is that the roles created won’t necessarily align with existing corporate structures making it difficult to communicate about them or govern them properly.
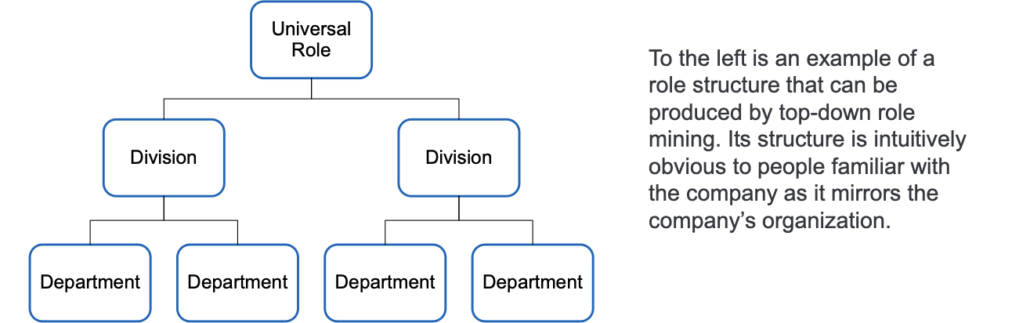
Top-down role mining finds roles candidates based on attributes that can be used to split a group of identities up into different populations. The access those populations have is then analyzed for commonalities in order to find the correct set of entitlements for each role. The advantage of the top-down approach is that the role candidates it discovers align with the population segments that the company is already familiar with. For example, in the role structure defined above, the organizational hierarchy of divisions and departments that can be seen on an org chart is mirrored in the role structure. The disadvantage to top-down role mining is that there is no guarantee that the access that people need has been assigned in the way the top-down role model is structured. This means that roles of limited utility with few people or few entitlements may make up the bulk of the role candidates.
In order to overcome the challenge of creating roles with values that also align with the structures that exist within a client’s populations, Edgile has developed a discipline called Role Model Analysis which we believe will change how roles programs are organized. Once we’ve discovered how a client’s role program should be organized, we know that to be successful we need to streamline the process of creating the roles within that structure, and we do that by setting up a client’s Role Factory enabled with SailPoint’s IdentityAI technology. To learn more about Edgile’s solution visit our RBAC page or contact the Edgile Identity team.
Connect with Edgile to get started
For details on how to optimize your identity programs, please contact your Edgile representative.

















