Services › Information Security › Zero Trust
INFORMATION SECURITY
Transitioning to Zero Trust
The recommended approach to securing the modern enterprise
Zero Trust is the modern security model
A Zero Trust foundation is the best way to modernize security, manage and investigate risk, and defend against threats. It’s built around three principles:
- Verify explicitly—Always authenticate and authorize based on all available data points, including user identity, location, device health, service or workload, data classification, and anomalies.
- Use least privileged access—Limit user access with just-in-time and just-enough-access (JIT/JEA), risk-based adaptive polices, with data protection to help secure both data and productivity.
- Assume breach—Minimize blast radius and segment access as you verify end-to-end encryption and use analytics to get visibility, drive threat detection, and improve defenses.
Zero Trust is the digital transformation security model advocated by government and industry because it:
- Links identity, security, information and compliance with cloud-powered intelligence
- Applies modern protocols for all app access, including web, SaaS and legacy
- Offers a path to risk-based access and passwordless authentication.
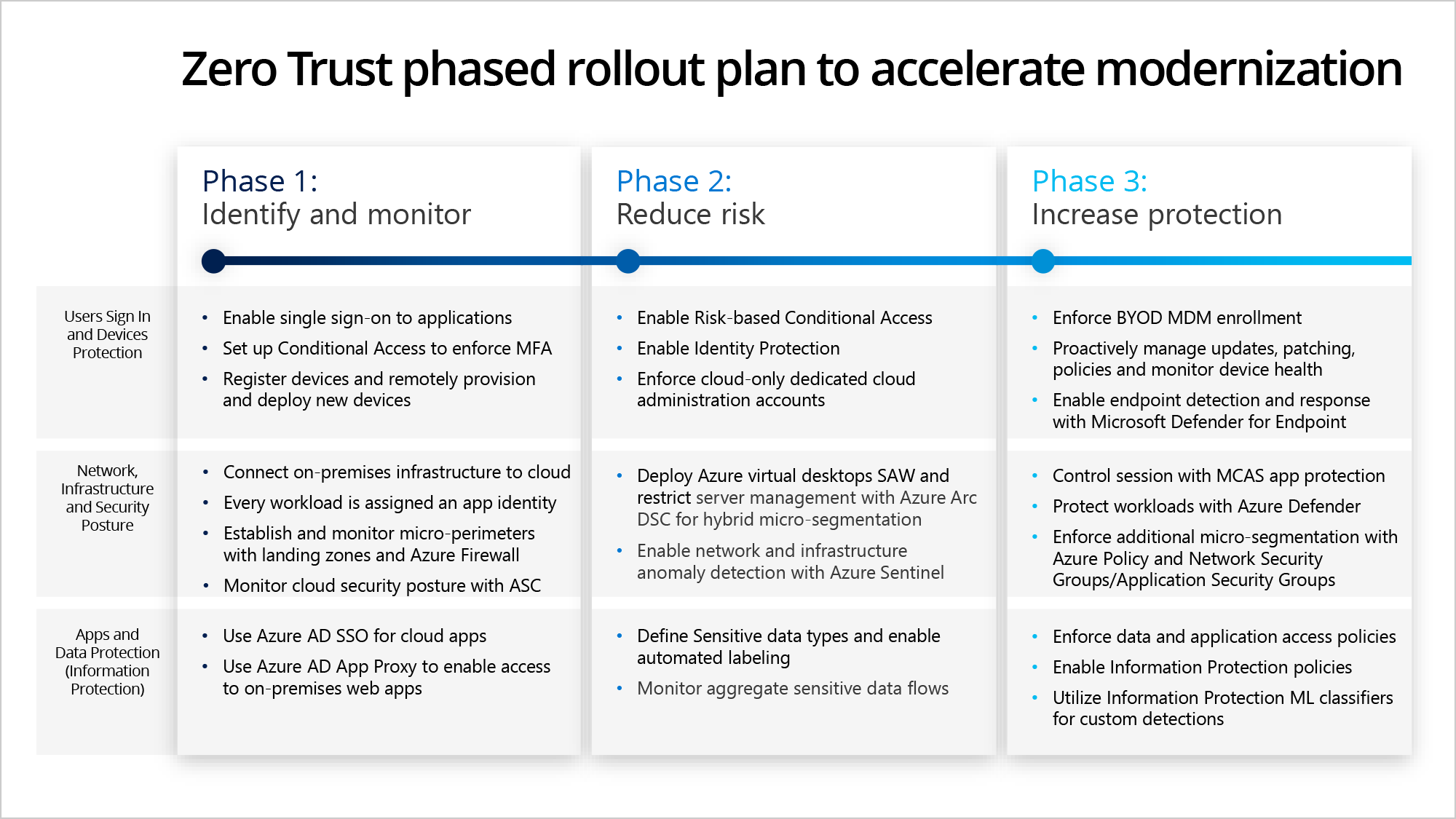
Zero Trust— the government- and industry-endorsed security model for digital transformation
Outdated security models and unencrypted data have led to an exponential rise in cyberattacks and ransomware. Business leaders all over the world are recognizing that threats to network and data security have overtaken the ability of traditional security solutions to provide sufficient protection.
In May, 2021, the White House issued an executive order on improving the nation’s cybersecurity, including the employment of a Zero Trust security model focused on five pillars—Identity, Device, Network, Application Workload, and Data.
Microsoft—Edgile’s recommended Zero Trust solution
Edgile believes Microsoft offers the best Zero Trust solution because of the visibility M365 E5 provides across the digital estate. In addition, Microsoft is positioned as a Gartner Magic Quadrant leader in:
- Access Management
- Cloud Access Security Brokers
- Enterprise Information Archiving
- Endpoint Protection Platforms
- Unified Endpoint Management
“Gartner estimates that 60% of businesses will shift to Zero Trust by 2023.”
Organizations that default to Microsoft gain the economic benefit of vendor consolidation and avoid integration costs. Edgile recommends that enterprises budget for above trend line spending over 12-24 months to deploy a Zero Trust model as soon as possible. Edgile can provide a roadmap and help you leverage your current investments in identity, security, and compliance while migrating to the Microsoft platform.
Connect with Edgile to get started
For details on how to modernize and secure legacy apps, please contact our Information Team.











