A multi-part blog series by Edgile’s Co-founder and a leading Microsoft MVP
It’s time to transform risk into opportunity.
Authors: Dean Fantham, Partner and CTO and Sean Deuby, Senior Architect

Corporate IT is almost never the first business unit to adopt cloud services. And if IT is making some tentative ventures into it, the business units are moving forward as quickly as they can. How do you help the business units continue their speed – or at least not get in their way – while still managing the risk these decentralized activities bring about?
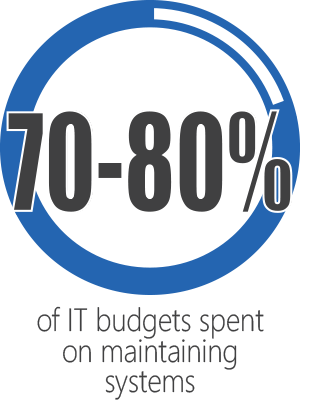
A major reason business units are doing this is because IT can’t respond quickly enough. Typically, 70-80% of an IT budget is typically spent on maintaining the complicated web of existing corporate systems, leaving little time or money for innovation. Add to this the IT organization’s traditional position as a cost center, rather than a profit center or business enabler. This leaves IT habitually understaffed, that very rarely has time or resources to stay abreast of trends.
Business units, on the other hand, look closely for any new trends or capabilities that might make them more competitive in the marketplace. The major cloud services are releasing hundreds and sometimes thousands of changes on an almost daily basis – and traditional IT suffers from the comparison. The business units are taking advantage of these changes at their own speed for their customers.
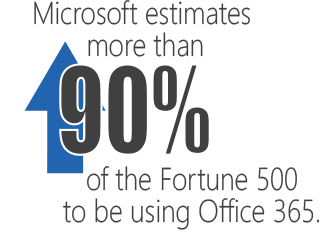
Office 365 is a prominent example. Businesses have rapidly adopted this cloud productivity suite (Microsoft estimates more than 90% of the Fortune 500 to be using Office 365), but in the haste to begin using it, many basic security controls have not been established – indeed even understood. Microsoft has not made this goal any easier; security controls and policies are scattered across at least 8 different products and consoles. As a result, CSOs find themselves scrambling to secure the cloud applications their businesses embraced without Security’s buy-in because “security isn’t their problem, it’s the cybersecurity team’s problem”.
What can a CSO offer the business? The CSO is the risk partner of the business teams. They need to provide the decision models and guidance to help business decisions makers recognize when there is increased risk to customers or the organization, to help them understand how the CSO function can support them to mitigate and find solutions and be the BDM’s safety blanket. This means the CSO needs to understand the data the organization handles, the threat and vulnerability model associated with various usage models and bring that into patterns and guidance for business partners.
What steps should a CSO and their team take to begin integrating with their business units again?
- Inventory and understand the organization’s cloud app usage. Understand what lifecycle controls are being used, if any, and what types of data that are going into and coming out of the app. Are the application’s controls appropriate for the type of data it’s consuming? Talk to the teams using the app to get a deeper understanding of their business needs; don’t just be the security guy. This work doesn’t take the place of a systematized SaaS app discovery process (perhaps with a CASB tool), however, because these groups don’t see the whole picture. You must combine both to get a complete overview of your organization’s activities and associated risk.
- Classify apps by risk and usage to prioritize your approach and develop appropriate processes and controls for each tier. This is also where the comprehensive discovery process may point out areas where app capabilities overlap that can be optimized for cost savings. These processes and controls (for example, MFA for high business impact apps) need to manage risk and provide corporate visibility while still minimally impacting businesses. This allows business units to get out of doing identity management and focus on their business.
- Manage app security and identity lifecycle by integrating it into a federated, delegated security model. Once integrated, security can then carefully apply more conditional access and controls with a goal towards not hindering the business, but helping it, while controlling risk. The challenge for the CSO is that they can’t use the old draconian security model; they must be highly responsive to the business unit. Mitigating who has access to the app, minimizing the proliferation of identity stores, and handling the deprovisioning problem alone will yield significant security benefits (and potentially subscription licensing savings) without negatively impacting the business.
- Rinse, repeat. This is not a one-time action, but an ongoing process. Monitor / discover app usage, classify, onboard into the framework and management.
Read blog #4 in this series, Protecting Your Enterprise Applications with Identity-Based Security.
















