Author: Sean Deuby, Architect
At Cloud Identity Summit in June, Microsoft’s Senior Product Marketing Manager Mary Lynch and Ping Identity’s Senior Director of Product Management Lee Howarth announced that they had entered a partnership that focuses on making a wide variety of on-premises applications available from outside the corporate network. Partnerships come and go in this business, but I think this one is worth noting because of the precedent the Microsoft Azure AD team is setting.
What is the partnership?
 The partnership focuses on two of Ping Identity’s most successful products, PingAccess and PingFederate, and their relationship with Microsoft’s Azure Active Directory. PingFederate is Ping’s flagship product, a broadly featured, federation-based SSO solution used by more than half of the Fortune 500. PingAccess provides single sign-on (SSO) and remote access to on-premises applications; relevant to this partnership, it supports older applications by transforming newer authentication protocols (such as Kerberos, SAML, and OAuth 2.0) into something the old apps can use, like header-based authentication.
The partnership focuses on two of Ping Identity’s most successful products, PingAccess and PingFederate, and their relationship with Microsoft’s Azure Active Directory. PingFederate is Ping’s flagship product, a broadly featured, federation-based SSO solution used by more than half of the Fortune 500. PingAccess provides single sign-on (SSO) and remote access to on-premises applications; relevant to this partnership, it supports older applications by transforming newer authentication protocols (such as Kerberos, SAML, and OAuth 2.0) into something the old apps can use, like header-based authentication.
Organizations that have purchased a subscription to Azure AD Premium or any of the larger suites (such as Enterprise Mobility + Security or Secure Productive Enterprise / Microsoft 365) will be able to use PingAccess – called PingAccess for Azure AD – to provide SSO in Azure AD for up to 20 on-premises applications. Integrating more applications will require a full PingAccess license. The PingFederate aspect of this partnership is that support for the product will be included in the Azure AD Connect configuration wizard.
Remote access without VPN for all your applications
To understand the partnership, you must first understand that Azure AD already has a feature – Azure AD Application Proxy – that allows an organization to publish on-premises applications into Azure AD. This makes the application securely available via an external URL and thus users don’t have to fire up a VPN to access it. You might think of App Proxy as “remote access as a service”. Access to the app is protected by Azure AD or application authentication, and access can be further controlled by conditional access (for example, requiring multi-factor authentication when a user attempts to login from a risky location).
If Microsoft has Azure AD Application Proxy, why incorporate PingAccess into the solution? Azure AD Application Proxy only supports modern identity standards such as Kerberos, SAML 2.0, and OAuth 2.0. This leaves a wide swath of old on-premises applications out in the cold, as most don’t use these standards. Enter PingAccess. By integrating PingAccess with Azure AD Application Proxy, the tens of thousands of organizations that use Azure AD can now publish essentially all their on-premises applications into Azure AD.
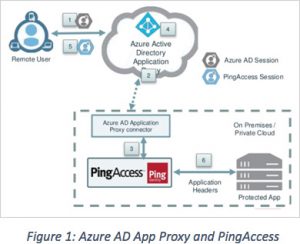 On the PingFederate side, the Azure AD Connect setup wizard (which configures identity synchronization and single sign-on between Active Directory and Azure AD) now includes PingFederate as an option. This makes it much easier for organizations using PingFederate as their identity federation service to set up single sign on to Azure AD.
On the PingFederate side, the Azure AD Connect setup wizard (which configures identity synchronization and single sign-on between Active Directory and Azure AD) now includes PingFederate as an option. This makes it much easier for organizations using PingFederate as their identity federation service to set up single sign on to Azure AD.
Who benefits from this partnership?
Besides making sense technically, I think this announcement is interesting because it’s an indicator of the Azure AD team’s willingness to partner with other vendors to integrate their capability into the Microsoft product. (Microsoft took a similar approach not long before this announcement, partnering with SailPoint to provide identity governance directly to Azure AD.) They’ve not done this before, and historically Microsoft as a whole has stayed away from this model; they preferred to build up functionality to a certain minimum level, then leave further enhancements to the ISVs.
Faced with a gap in their product suite, Microsoft had three choices: Build, buy…or partner. The company recognized that they don’t have expertise in this particular area and it would take too long to develop it, and they can’t buy Ping (the product suites don’t match up well, and Ping was bought by a private equity firm anyway). Thus, it makes sense for Microsoft to partner with a company that has precisely the product it needs.
Regarding PingFederate, it’s simply Microsoft’s recognition that this product is well entrenched in its customer base; according to Azure AD statistics it’s the most popular third-party federation or cloud service authenticating users to Azure AD – by a factor of 2x. The company no longer pretends that other good products simply don’t exist.
What does Ping get out of this deal? Brand and product exposure to one of the world’s largest collection of organizations: Azure AD tenants. 11 million organizations have a tenant in Azure AD. 90% of the Fortune 1000 use Office 365, and thus have an Azure AD tenant. Almost 40K EM+S subscriptions have been sold, and these subscriptions contain Azure AD Premium and thus PingAccess. That’s a lot of eyeballs on the Ping brand, and most of these subscriptions have on-premises apps that could use PingAccess. The company will also get PingAccess licenses for organizations that need to integrate more than 20 applications, but I think that will be a relatively small percentage of customers. It’s also a strong Microsoft endorsement of Ping to all these companies, selling potentially other Ping products to them.
Microsoft dramatically broadens its on-premises application coverage and Ping gets vast exposure. But it’s the Azure AD organization who really wins: they will be able to make most of their on-premises apps securely available in the Azure AD cloud service. I look forward to seeing what other partnerships result from this new strategy.
















