Overcoming the challenges in adopting a Zero Trust cybersecurity approach
By Gretchen Wichmann, Tarun Vazirani, and Josh Salton
Get the eBook
The Power of an Integrated Approach to Zero Trust Cybersecurity
What is a Zero Trust model?

As its name implies, Zero Trust assumes that no identity—be it an employee, a service provider, or a connected device—is inherently trustworthy. Every access request must be fully authenticated, authorized, and encrypted before access is granted, regardless of origination inside or outside the network or which resource is being requested.
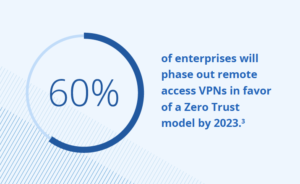
As the majority of the world’s businesses move into the cloud and out of the traditional network perimeter,1 Zero Trust has become an increasingly common approach to cybersecurity. In fact, by 2023, 60% of enterprises will phase out remote access VPNs in favor of a Zero Trust model.2
This shift has not been without its challenges, however. Here we explore four of the most common barriers companies face when adopting a Zero Trust approach – and how to overcome them.
Challenge #1: How do I adapt a Zero Trust model?
When organizations turn to a Zero Trust framework, they often don’t know where to invest and how to prioritize this transformation. Zero Trust controls and technologies are found across six foundational elements: identities, devices, applications, data, infrastructure, and networks. This can seem overwhelming when first getting started.
- The fix: Building Zero Trust into your organization should always start with a tactical, phased roadmap, starting with a maturity assessment of your Zero Trust readiness. This will help ensure that each investment and step forward on your Zero Trust journey is aligned with your current and future business needs.
Challenge #2: A remote and dynamic workforce

The COVID-19 pandemic forced many Americans to work from home – some for good. As of April 2021, 52% of all workers, including 72% of those in white-collar occupations, were still performing all or part of their jobs remotely.3 Consumers, too, are conducting more transactions online. This surge in utilization of home IPs, routers, public WiFi, and VPN services has created a vast, varied, and ever-expanding base of users who need remote access to data. Add to the mix high turnover for both employees and customers, and IT security teams can quickly become overwhelmed.
- The fix: An identity security platform that uses artificial intelligence and machine learning to automate access provisioning, ensuring that the right people have the right access at all times.
Challenge #3: Endless choices
Not only are there more users than ever before, but there is also an unprecedented number of devices, platforms, applications, and technologies available for business and personal use. What’s more, business and personal use are increasingly intertwined in this new remote reality. The result is a complex web of different properties, requirements, and communication protocols that must be maintained on an ongoing basis. Many companies lack the expertise and resources to handle this responsibility, resulting in increased risk of exposure to cybercrime.
- The fix: An identity security solution that integrates with multiple applications for secure, seamless sign-on across various systems.
Challenge #4: Potential for downtime
One potential downside for restricting access in a Zero Trust model is the productivity bottlenecks that may occur as a result. When – not if – the access needs of an individual inside or outside the company change, the individual could be blocked from the tools they need to do their job.
- The fix: An identity security solution that migrates existing customer accounts automatically to provide a seamless user experience – with minimal downtime.
An integrated approach to securing the modern enterprise
Edgile has developed a comprehensive, integrated approach for organizations looking to move from a perimeter-based security concept to a Zero Trust framework. Our solution leverages strengths from two principal leaders in our partner network: Microsoft and SailPoint.

Read the eBook on the power of Zero Trust

Download our eBook, “The Power of an Integrated Approach to Zero Trust Cybersecurity,” to learn how we can help you:
- Secure workforce access to cloud and on-premises applications in minutes instead of weeks.
- Ensure that only the right users have access to the right applications.
- Mitigate internal and external risk of threat.
Connect with Edgile to get started
For details on how to optimize your identity programs, please contact your Edgile representative.
1 2020 IDG Cloud Computing Study. IDG.
2 Avast Blog. “What Is Zero Trust Network Access?” Security Boulevard. May 2021.
3 Lydia Saad and Jeffrey M. Jones. “Seven in 10 U.S. White-Collar Workers Still Working Remotely.” Gallup. May 2021.
















