By Dan Seyer, Edgile CMO

One of the key problems with security software today is how well it interacts with other apps in the enterprise. Whether it’s anti-virus that has a software conflict or a threat detection system that gets confused by a new VPN, security software has a reputation of not playing well with others.
Microsoft is working to change that. Their new security suite—Microsoft Azure Sentinel—was designed from the beginning to co-exist within Azure. This cloud-native SIEM for intelligent security analytics and security orchestration automated response (SOAR) system leverages more than $1 billion of annual cybersecurity investments and accesses the talents of more than 3,500 global security specialists.
One of the benefits of working with Microsoft—which currently serves more than 96 percent of U.S. Fortune 1000 companies*— is their extensive view of the current industry attack efforts. This enables Azure Sentinel to use AI machine learning to analyze trillions of diverse signals for unparalleled intelligence. Azure Sentinel has near-real-time access to the specifics about any attacks being used against almost any Fortune 1000 company. That’s a powerful security advantage.

Another key advantage with Microsoft Azure Sentinel is seamless tool integration for customers already using Microsoft products and services. A massive CISO challenge with most SIEMs is making sure that the SIEM has visibility into as much data as possible and that the integration is simple. Azure Sentinel uses standard log formats and needs no infrastructure setup or maintenance and the SIEM service is available from within your existing Azure portal. CISOs can easily bring over Office 365 data for free. It uses a proven log platform with more than 10 petabytes of daily ingestion. Security can immediately use existing machine learning models along with threat intelligence feeds.
Microsoft Azure Sentinel also addresses the scalability needs of Fortune 1000 companies, whether from pure revenue growth or M&A activity. The SIEM scales automatically, leveraging the Microsoft cloud to deliver compute or storage resources with virtually no limits.
This allows your security teams to collect security data at cloud scale from all sources across your enterprise, unburdening SecOps from routine IT tasks.
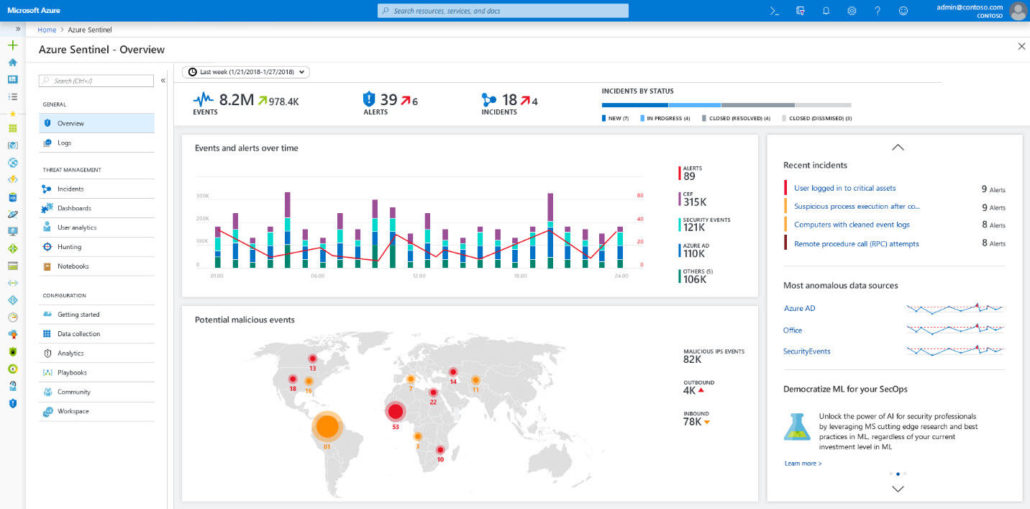
Another major enterprise security challenge today is customizing threat intelligence feeds based on specific geographies, verticals and security postures. Azure Sentinel includes machine learning models and UEBA based on decades of Microsoft security experience and learnings. The pre-integrated models quickly filter millions of signals down a handful of correlated and prioritized incidents leveraged from both the vast Microsoft threat intelligence data and cross-checked against your enterprise’s own threat intelligence feeds. This can slash alert fatigue by as much as 90 percent.
Azure Sentinel comes with powerful hunting search-and-query tools, based on the MITRE framework which allows security teams to hunt for suspicious activities before an alert is triggered using pre-built queries and Azure Notebooks. CISOs can also easily build automated and scalable playbooks that integrate across tools. And the ticketing systems flow effortlessly via ServiceNow.
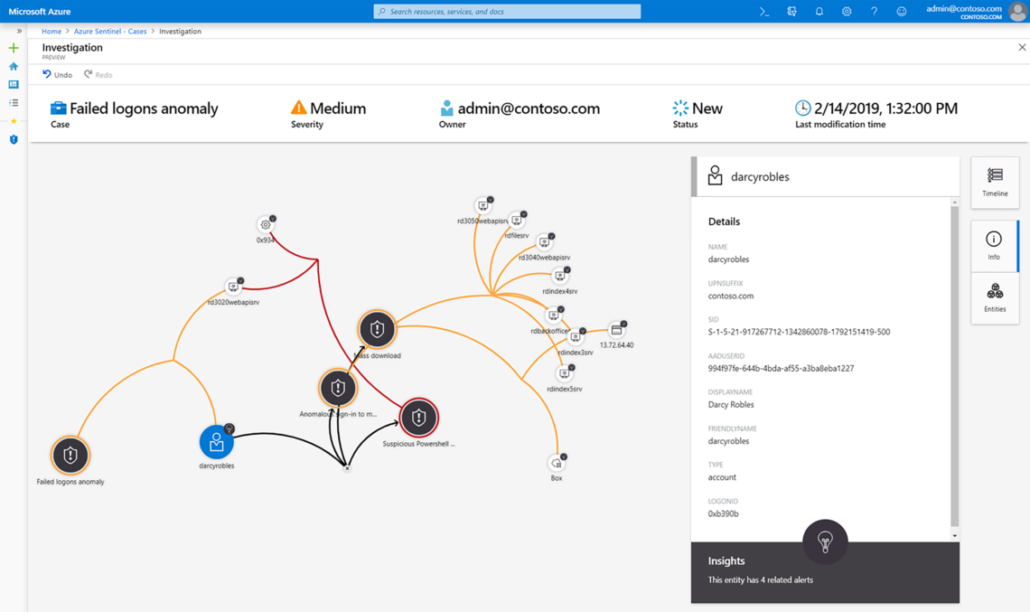
Once the team finds high-value insights into possible attacks, team members can create custom detection rules based on that query and surface those insights as alerts to security incident responders. While hunting, team members can create bookmarks for interesting events, enabling them to return to them later, share them with others, and group them with other correlating events to create a compelling incident for investigation. Team members can also download sample content from the private community GitHub repository to create custom workbooks, hunting queries, notebooks, and playbooks.
Building on the full range of existing Azure services, Azure Sentinel natively incorporates proven foundations including Log Analytics and Logic Apps. It comes with several connectors for Microsoft products available out of the box and providing real-time integration, including Microsoft Threat Protection and Microsoft 365 sources, Office 365, Azure AD, Azure ATP, and Microsoft Cloud App Security. Security teams can use common event format, Syslog or REST-API to connect data sources. Azure Sentinel includes more than 200 connectors for Azure services that allow security teams to apply any custom logic in code, ServiceNow, Jira, Zendesk, HTTP requests, Microsoft Teams, Slack, Windows Defender ATP, and Cloud App Security. There are also built-in connectors for security and productivity apps outside of Microsoft.
















