MODERN IDENTITY SOLUTIONS
Modern Privileged Access Management
Information security through an administrative access lens

Establish, advance or reset your PAM strategy
Privileged Access Management (PAM) teams are tasked with creating effective and secure access for both internal and external users while remaining one step ahead of the bad actors. Yet many organizations struggle with prioritizing, justifying, and executing an effective PAM strategy.
Edgile’s risk-based PAM strategy develops a plan that protects your privileged accounts and highlights and prioritizes necessary controls for infrastructure and applications, including:
- Password and secrets management
- Security integration and analytics
- End point least privilege
- Secure remote and vendor access
- Organizational change management
We can create or reset your PAM program with installation, migration, upgrades and onboarding. You get the support you need to accomplish your immediate goals, and the KPIs to ensure ongoing success.
Edgile’s Privileged Access Management framework
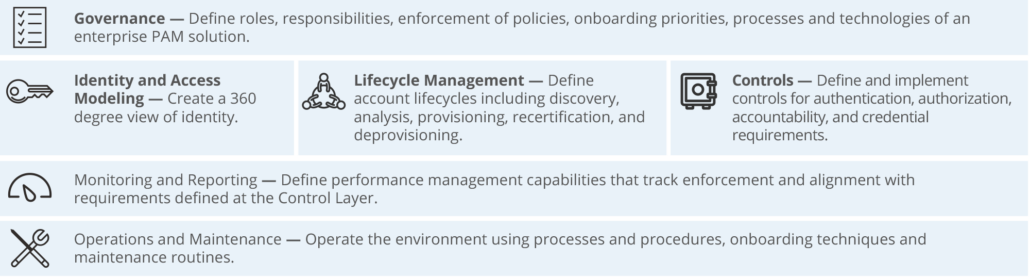
Guiding Principles to Prevent Privileged Abuse

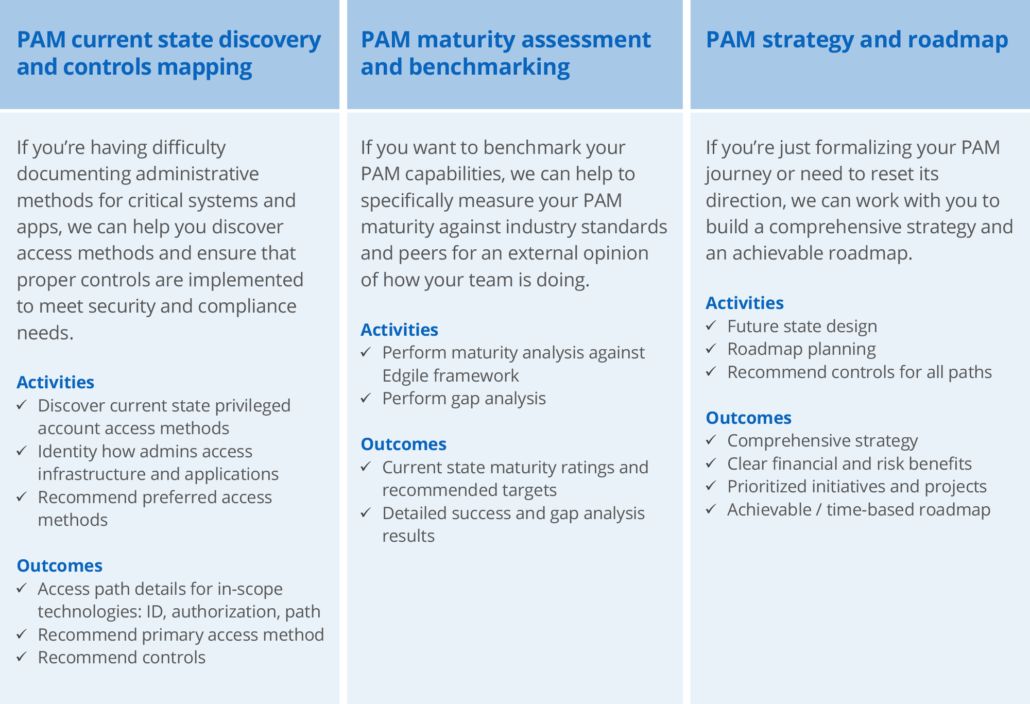
Select the PAM strategy aligned to your objectives
We understand that your Privileged Access Management journey is unique to your organization, and that over time, changing strategies, direction, priorities, and technology can affect how much help you need, where you start out, and how your program evolves.
Edgile offers three PAM strategy engagements, each targeted to a different need and jumping off point.
1 Source: 2020 Verizon Data Breach Investigations Report

Connect with Edgile to get started
For details on how we can help formalize your PAM program, please contact our ldentity Team.



















