Services > Information and Cloud Security
MODERN INFORMATION SECURITY SOLUTIONS
Information and Cloud Security
Information and Cloud Security Solutions
Information security is viewed by most organizations as a risk mitigation activity. This view has been reinforced by security professionals, governance processes, and traditional security approaches.
The information landscape of the future is dotted with cloud computing infrastructure, virtual global workforces, information at your fingertips, and dynamic collaboration technologies. The need to compete and win in the market, reduce cost, and spur innovation is driving organizations to embrace cloud security.
Edgile’s information and cloud security approach shifts an organization’s viewpoint from purely risk-centric function to a hybrid risk and business-aligned capability, turning security into a strategic business enabler for the enterprise.
STRATEGY
We provide a strategy-first approach to drive program success.

IMPLEMENTATION
We enable controls in the cloud for all users, including employees, partners, third party vendors, and clients.
MANAGED SERVICES
We provide managed services to help run your security program
Edgile Value Differentiators

Start with strategy
A strategy defines how an organization will invest its limited resources to protect sensitive information and intellectual capital. The strategy sets your compass to ensure your success is achieved at the correct scale to enable your organization.

Quick Start configurations
Quick Starts are designed to jump right into a mix of strategic thinking and implementation. In a matter of weeks, our experts will implement what you need to get started and you’ll know what to do next. Quick Starts have a defined outcome plan and use a proven model to achieve predictable results.
Information security and industry expertise
You’ll benefit from a leadership and implementation team that has led hundreds of implementations across industries just like yours—with projects ranging from strategy to program development to implementation, change management, training, and managed support.
Use strategy to drive information security investments
Information security plays a key role in ensuring that strategic capabilities are securely planned, developed, and implemented. Edgile’s security approach starts with the business strategy and business goals. We then define the strategic capabilities from a security perspective in conjunction with the business and IT groups. This interaction is critical to the process and facilitates the alignment between the security groups and business. Typically, focusing on a business-aligned security strategy produces improved results compared to a risk-centric only approach.

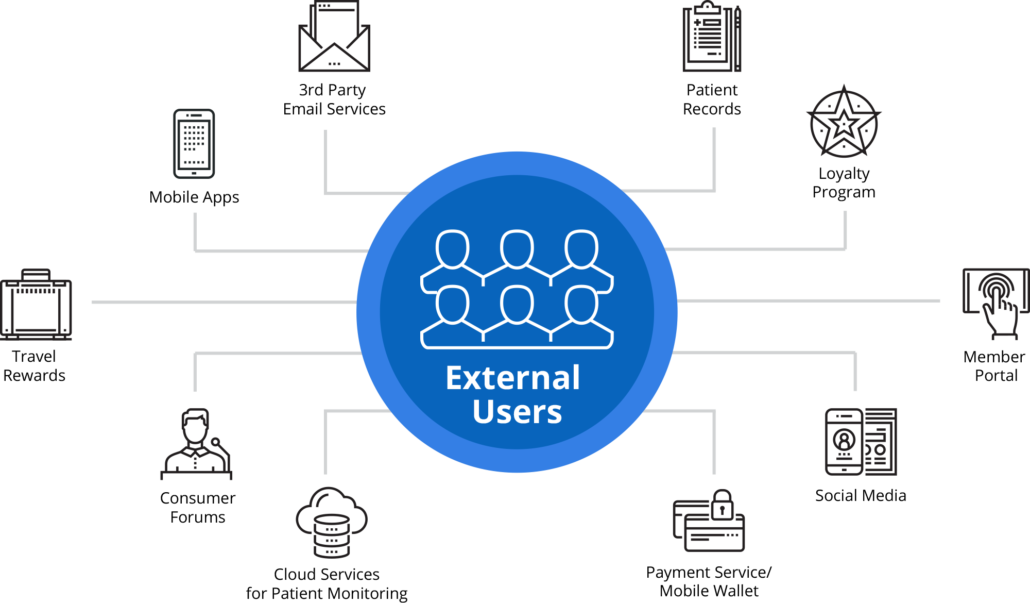
Information security for external users
Information security for users operating outside the enterprise presents additional challenges because it focuses on the consumer experience. These individuals are given access to services or systems you provide and include consumers in the retail, food or travel industry, patients in the healthcare industry, or subscribers to an online or mobile service.
These users trust your business to secure their personal information and want full control over how much information is shared and with whom. In healthcare, for example, a patient who subscribes to a service that provides lab results will want the ability to choose which test results are shared with certain doctors or family members. Or a retail consumer may authorize the retailer to access his or her birthdate for loyalty program purposes, but may choose to opt out of third-party promotional emails. Learn more about External Identities
Zero Trust

Organizations need ways to reduce risk, accelerate modern authentication processes and increase end-user productivity—particularly in today’s remote workforce environment. A major challenge in this effort is integrating on-premises legacy applications into a comprehensive app management strategy with cloud intelligence and modern auth.
Azure External Identities
Modern enterprises have various access portals and apps with legacy branding requiring multiple login credentials and passwords. This creates disparate and confusing user experiences in addition to security risks. It’s not only frustrating for the customer, it prevents the organization from having visibility into the customer experience, and can lead to data isolation, development complexity and identity duplication.
Threat Protection (SIEM & XDR)
User Experience

Optimized for users and security
Learn more about Edgile solutions
Optimizing Microsoft 365 control settings for reduced risk in the cloud
As a trusted Microsoft Gold security partner, Edgile has developed four detailed Microsoft 365 Configuration Guides offering pre-engineered control settings for Microsoft…
Continue Reading Optimizing Microsoft 365 control settings for reduced risk in the cloud
Edgile’s Microsoft 365 Security and Compliance Solution
Edgile’s Microsoft 365 Security and Compliance Solution delivers a strategy-first integrated risk management approach, aligning IT with compliance and privacy across the…
Continue Reading Edgile’s Microsoft 365 Security and Compliance Solution
FastTrack for Microsoft 365
FastTrack is a service provided by Microsoft and delivered by Edgile to help large, regulated enterprises deploy Microsoft 365 cloud solutions and drive…
Connect with Edgile to get started
For details on how we can help formalize your Information Security program, please contact our Information Security team.

























