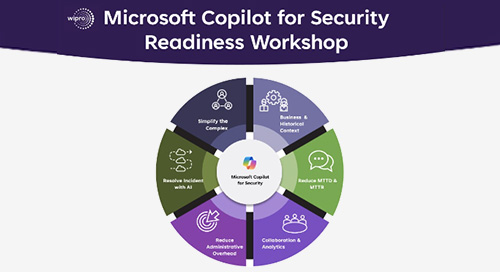
Exponential Thinking for IT Adoption: Cybersecurity in the Era of AI
By Bob Moore, Partner, Wipro Cybersecurity and Risk Services Group
History is filled with cautionary tales of those who rush ahead, only to find themselves exposed and vulnerable. Today, we see this unfolding in the adoption of Generative AI (GenAI). While businesses are modernizing processes to think exponentially and respond swiftly (think OODA Loop), IT is one critical area that is lagging behind — particularly in the realm of cybersecurity.
The Growing Cybersecurity Challenge
GenAI continues to advance, transforming industries and revolutionizing processes, promising to exponentially enhance human experience and productivity. However, this rapid pace of adoption introduces new and unprecedented cybersecurity risks.
Traditional IT structures, developed 10-15 years ago for a different era, are ill-equipped to handle the complexities of GenAI-driven environments.
In the 1990s, having specialized teams for identity, messaging, and end-users made sense. However, times have changed. Today, with cloud signals being sharable across the IT landscape and Zero Trust requiring comprehensive visibility, maintaining a structure focused on functional optimization is outdated.
The old playbook of cybersecurity, relying on perimeter defenses and siloed teams, is insufficient in an age where cyber threats are increasingly sophisticated and AI-powered. Cyber adversaries are leveraging AI to automate attacks, quickly identify vulnerabilities , and execute complex strategies — all with unprecedented speed. In this context, organizations are struggling to achieve a Zero Trust framework because of disjointed products and varied priorities. The traditional tech acquisition process exacerbates this issue. While detailed vendor investigations are necessary, running RFPs and conducting bake-offs for mature capabilities wastes resources and hinders agility.
The Imperative for Zero Trust Security
To combat these new threats, organizations must embrace exponential thinking within their IT structures, especially in cybersecurity. This shift requires moving away from outdated models and adopting a proactive, adaptive approach that leverages GenAI and advanced technologies to stay ahead of cyber adversaries.
The security model for AI is Zero Trust. If more enterprises could have successfully adopted Zero Trust two or three years ago, security postures would be AI-ready now. Unfortunately, despite market and government support, Zero Trust proved challenging to implement. The obstacle lies in our IT structure and lack of exponential thinking. If we had fully understood the importance of comprehensive data repository knowledge, access control, session management, and end-to-end visibility, we might have driven this change earlier.
Exponential Thinking: A New Approach to Cybersecurity
Previously, IT departments evaluated, acquired, and integrated distinct products across various categories. Now, many workloads have become commodities, and IT’s role should shift to configuring vendor platforms. By shifting commodity workloads to platform vendors, IT organizations can free themselves from outdated technologies and processes, effectively acquiring exponential thinking as a service from companies designed to think and act rapidly.
This shift is particularly crucial for cybersecurity in the era of AI. Relying on traditional, siloed security tools and methods is a recipe for disaster. Instead, organizations need integrated, AI-driven cybersecurity platforms that provide comprehensive visibility with real-time threat detection and response. This approach not only enhances security but also enables IT to act as a strategic enabler for business growth.
Implementing the Shift: Best Practices
To foster this thinking, create an Enterprise Zero Trust Collaborative Group comprised of like-minded functional leads. Empower this group to execute a platform-centric strategy. Reform the business-as-usual model by instilling continual re-evaluation of the environment, situational awareness, business, threat, and group responsiveness metrics. Integrate closely with your platform provider, leveraging their exponential thinking. Include your managed service providers and challenge them to adopt the same approach.
Develop an agile framework for capability enhancement that matches platform evolution. Create your own OODA Loop process and continuously optimize it. This will ensure that your organization can rapidly adapt to new threats and proactively leverage AI to enhance security measures.
The Path Forward: Embracing Exponential Security
The adoption of AI brings both unprecedented opportunities and significant cybersecurity challenges. To thrive in this new era, organizations must transform their IT structures and embrace exponential thinking. By doing so, they can build resilient, adaptive, and AI-ready cybersecurity frameworks that safeguard their future in an increasingly digital world. It will enable the organization to act faster, be more responsive, reduce costs, and empower teams across the enterprise to think exponentially.
Connect with Edgile to get started
For details on how to optimize your information security programs, please contact your Edgile representative.