Services > Identity and Access Management Solutions
MODERN IDENTITY SOLUTIONS
Identity and Access Management
Identity and Access Management Solutions
Enterprises need to modernize their identity programs. This can mean rebooting an existing program or starting a new program. Edgile has over 20 years of experience in modern identity solutions. We are the trusted advisor to 30% of the Fortune 100 providing identity strategy and implementation services.
STRATEGY
We provide a strategy-first approach to drive program success.

IMPLEMENTATION
We enable identity management controls in the cloud for all users, including employees, partners, third party vendors, and clients.
MANAGED SERVICES
We provide managed services to help run your program.
Edgile Value Differentiators

Start with strategy
An identity strategy defines how an organization will invest its limited resources to protect sensitive information and intellectual capital. The strategy sets your compass to ensure your success is achieved at the correct scale to enable your organizational goals.

Quick Start configurations
The Quick Start is designed to jump right into a mix of strategic thinking and implementation. In a matter of weeks, our experts will implement what you need to get started and you’ll know what to do next. Quick Starts have a defined outcome and use a proven model to achieve predictable results.
Industry Expertise
You’ll benefit from a leadership and implementation teams that have led hundreds of identity implementations across industries just like yours—with projects ranging from strategy to program development to implementation, change management, training and managed support.
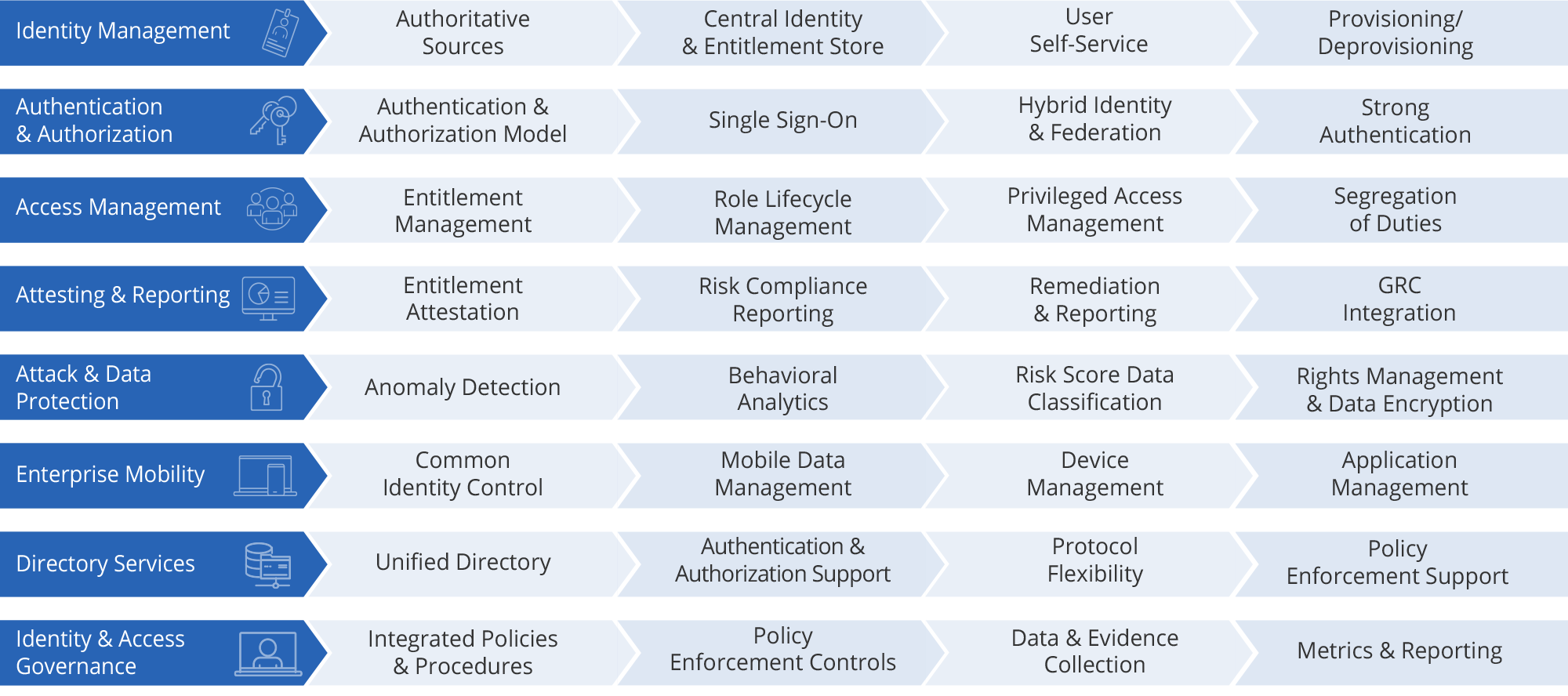
Identity Capabilities Framework
Edgile’s identity capabilities framework allows us to assess a company’s current state capabilities, define the future-state vision and develop a gap analysis, which is the foundation for an identity strategy and roadmap. We help you focus on driving business value by defining a holistic set of enterprise identity service capabilities ranging from day-to-day management of user access to compliance reporting.
Start with Strategy
Edgile’s strategy-first approach to IAM provides a critical foundation for long term success. We build a deep understanding of our clients’ current state environment, including risk factors, operational costs, regulatory needs, organizational constraints, technical architecture, and supporting business processes. We then develop a prioritized and structured roadmap for future success that is value-driven and aligns to well-established industry best practices.
Identity for Enterprises
Identity need to securely control access to resources, while meeting increasingly rigorous compliance requirements. The Edgile approach begins with helping you prioritize Identity capabilities around your key business drivers. By working together to define both current state and future state IAM business processes, we can more effectively align the program with your key stakeholders. Our efforts are organized in short project sprints that drive business value quickly, while managing risk to the complete IAM solution.
To ensure alignment with risk and compliance requirements, Edgile also helps you connect identity efforts with Governance, Risk and Compliance (GRC) capabilities to automate controls and support processes for identity and Privileged Access Management (PAM).
SailPoint Solution Spotlight
Establish, advance or reset your PAM strategy
PAM Spotlight
Privileged Access Management (PAM) teams are tasked with creating effective and secure access for both internal and external users while remaining one step ahead of the bad actors. Yet many organizations struggle with prioritizing, justifying, and executing an effective PAM strategy.
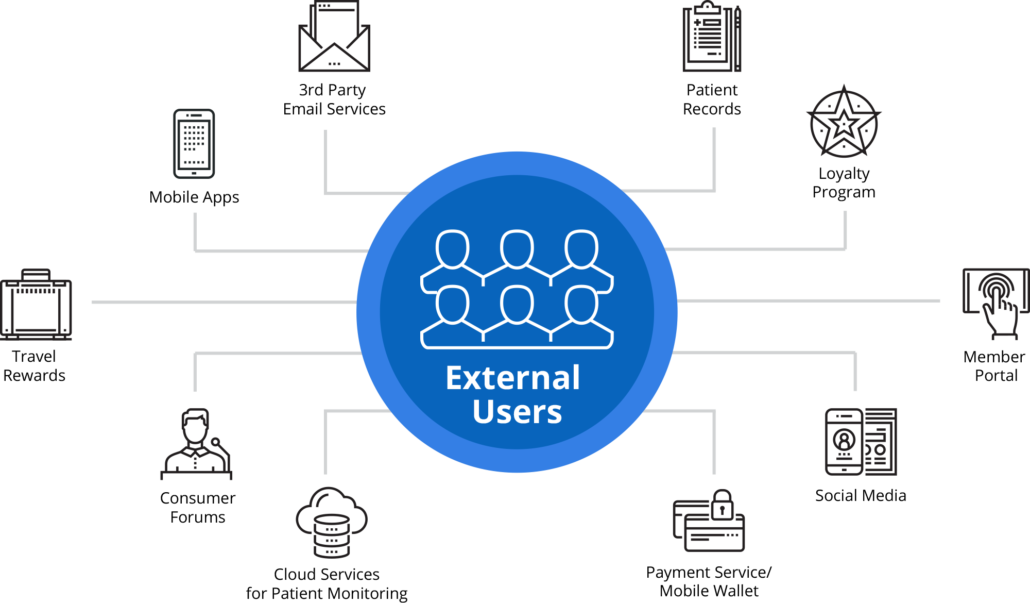
Identity for external users
Identity for users operating outside the enterprise presents additional challenges because it focuses on the consumer experience. These individuals are given access to services or systems you provide and include consumers in the retail, food or travel industry, patients in the healthcare industry or subscribers to an online or mobile service.
These users trust your business to secure their personal information and want full control over how much information is shared and with whom. For example, in healthcare, a patient who subscribes to a service that provides lab results will want the ability to choose which test results are shared with certain doctors or family members. Or a retail consumer may authorize the retailer to access his or her birthdate for loyalty program purposes, but may choose to opt out of third-party promotional emails. Learn more about External Identities
Customer Identity and Access Management (CIAM) Spotlight
Organizations today are in various stages of their digital transformation to the cloud. But all companies understand that the customer experience has always driven successful business transactions. Customers expect a seamless, intuitive online experience while also feeling safe and secure. Nurturing customer relationships to build loyalty while promoting brand awareness is at the center of the Edgile user experience approach. Our deep expertise in modern platforms and legacy systems allows us to build integrated CIAM solutions that are scalable to your growing user base. This reduces complexity so administrators can add, manage, and provision permissions to customers and employees with ease. The result is increased business productivity, decreased errors, and lower risk.
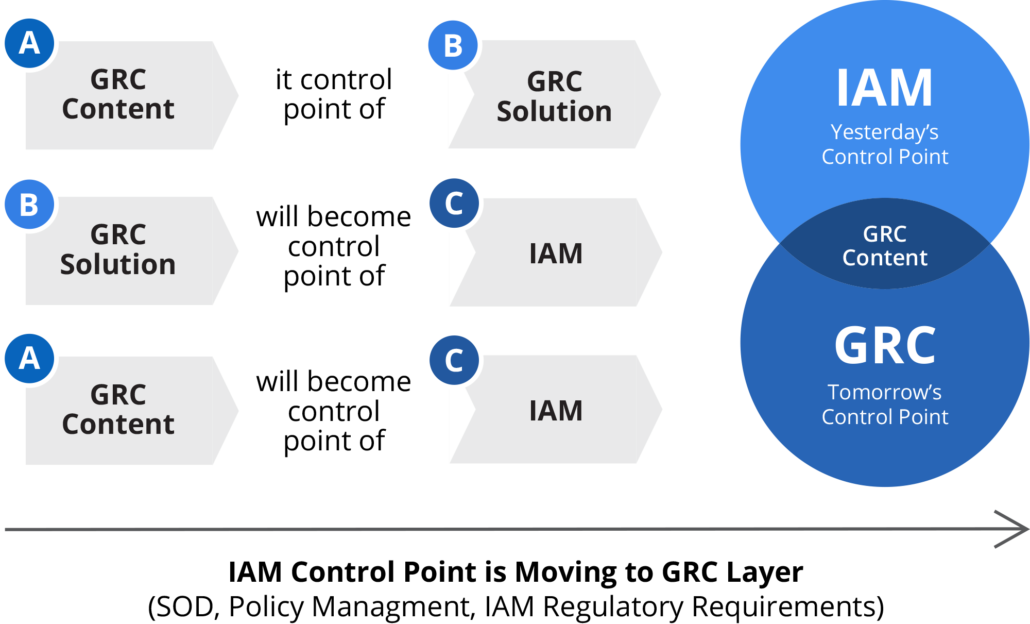
The identity control point is moving to GRC
The growing importance of identity is also being driven by governance, risk and compliance (GRC) requirements to ensure that companies continue to operate within the boundaries of changing regulations. The links between Identity and GRC are being strengthened to automate controls and support risk and compliance processes. Learn more about GRC/IRM ![]()
Learn more about Edgile solutions
Why Leading CISOs are Adopting a Strategy-First Approach to IAM
Learn how your company should benefit from a multi-perspective IAM plan. With mounting security threats and audit and regulatory deadlines, CISOs are…
Continue Reading Why Leading CISOs are Adopting a Strategy-First Approach to IAM
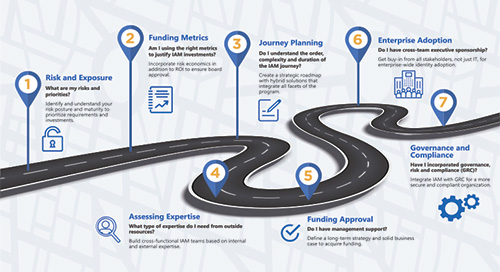
7 Key Considerations on the Road to High-Performing IAM
Are you asking the right IAM questions? Follow our infographic to start your journey. As you continue to purchase and implement IAM…
Continue Reading 7 Key Considerations on the Road to High-Performing IAM
The importance of Identity and Access as enterprises shift to the cloud
Business operations are becoming more complex as the number and type of users increases, coupled with their ability to access a growing…
Continue Reading The importance of Identity and Access as enterprises shift to the cloud
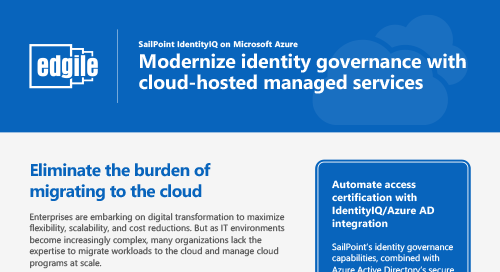
Modernize identity governance with cloud-hosted managed services
As IT environments become increasingly complex, many organization lack the expertise to migrate workloads to the cloud and manage cloud programs at…
Continue Reading Modernize identity governance with cloud-hosted managed services
Healthcare CISO Accelerators
Preventative Cybercare is Good Medicine for Your Security Program. Today’s cyber attacks can be inside networks for well over 200 days before…
Edgile Overview – We Secure the Modern Enterprise℠
The future of business is being driven by cloud computing, virtual workforces, and dynamic collaboration technologies. This rapidly evolving environment makes data…
Continue Reading Edgile Overview – We Secure the Modern Enterprise℠
The Power of an Integrated Approach to Zero Trust Cybersecurity
Cloud-based infrastructure is the foundation for digital transformation and is quickly becoming a must-have for modern organizations. In fact, 92% of the…
Continue Reading The Power of an Integrated Approach to Zero Trust Cybersecurity
Connect with Edgile to get started
For details on how we can help formalize your Identity and Access Management program, please contact our ldentity Team.








 Core Advisory
Core Advisory
 Risk & Compliance Transformation
Risk & Compliance Transformation
 Cloud, Zero-Trust & Enterprise Security Architecture
Cloud, Zero-Trust & Enterprise Security Architecture
 Identity & Access Management
Identity & Access Management
 Data Security & Privacy
Data Security & Privacy
 Cyber Defense and Response
Cyber Defense and Response