Author: Sean Deuby, Edgile Senior Architect, Microsoft MVP
A little over a month ago, a former colleague told me that the 18th anniversary of promoting the first domain controller of Intel’s corporate Active Directory forest had just occurred. Intel’s AD is now old enough to vote!
I was on the original team that designed and deployed Intel’s corporate Active Directory forest just a few months after the product was released in February of 2000. In a nice example of serendipity, I happened to be near Intel IT’s headquarters in Folsom, California, and was able to get together with a couple of the other key players on the original Intel AD engineering team. It caused me to reflect on how well AD has held up over the years, how much the world has changed since the product was released, and how Microsoft has adapted to the changes.

18 years is a LONG time for one product in the software world. How many other mission critical products can you think of that are still widely in use at that age? Yet Active Directory (more accurately Active Directory Domain Services) is still firmly entrenched in the heart of most corporate infrastructures, and I’ve not talked to anyone who is planning on taking it out any time soon. Indeed, I’ve seen a movement toward cleaning up and consolidating existing AD installations. These initiatives seem to be driven by two factors: General cleanup due to authentication issues caused by crusty old AD environments, and the need for a solid identity underpinning to cloud services such as Office 365.
The fact that Active Directory is still used in practically every organization with more than 500 employees, with largely its original architecture, is a testament to its robust and scalable design. But there’s no way the original AD product managers could have predicted the current digital landscape. In 2000, web services were pretty basic. Attacks were generally unsophisticated, looking to cause more mischief than financial gains for their perpetrators. There was no generalized mobile device app ecosystem. And I believe Amazon was still describing itself as a bookstore. As good as Active Directory is, it was designed at a time when the applications of today and the threats that face them didn’t exist.
That’s one of the reasons identity management as a service (IDaaS) was invented: to provide the same identity services for the world of web and mobile services as AD does for on-premises enterprise services. Active Directory provides single signon, authentication, and authorization services for applications and devices that are integrated into it. And at its simplest level, that’s also what IDaaS services such as Azure AD, Okta, PingOne, and others do.
iDaaS: A new service for a new world
Once you start to look a little deeper, however, the similarities end. Modern IDaaS services are based on an architecture — identity management outside the corporate perimeter, on someone else’s platform — that almost everyone from the enterprise world (including me) said when we first saw it, “Are you crazy? What corporation would ever do that?” Active Directory supports one organization (potentially with multiple forests), and collaborating with other organizations is difficult. iDaaS services are inherently multitenant, with thousands or millions of organizations using the service simultaneously. And the two services use completely different sets of protocols.
Complementary, not competitive
The key to understanding the relationship between AD and IDaaS services is that, for the vast majority of organizations, the two are complementary, not competitive. This is due to ADs incredible market penetration and organizations’ dependence upon the product: rather than throwing AD away and starting fresh in the cloud, companies elect a hybrid approach where AD is effectively extended into an IDaaS service (Figure 1). Once there, AD-sourced identities can be used to provide authentication and access management to SaaS services. This gives companies a unified identity system that is actually two.
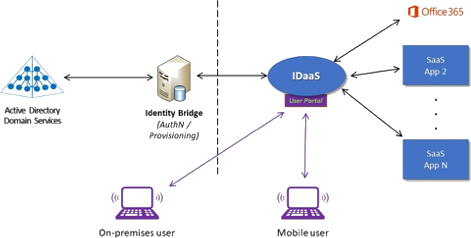
Figure 1: The Active Directory / IDaaS hybrid identity architecture
The hybrid model is the de facto standard for identity architectures that are based on existing on-premises identity systems such as Active Directory. As a consequence, Active Directory is now more important than ever because it’s the foundation for a much broader range of services and capabilities than could ever have been possible with AD alone. And of course, with this importance comes the need for clean AD data, modern threat detection, and disaster recovery.
Happy 18th, Intel AD. And to all its younger counterparts out there: the business world depends on you more than ever.










