IAM
The Power of an Integrated Approach to Zero Trust Cybersecurity
Cloud-based infrastructure is the foundation for digital transformation and is quickly becoming a must-have for modern organizations. In fact, 92% of the world’s businesses have… Read More »The Power of an Integrated Approach to Zero Trust Cybersecurity
Edgile Overview – We Secure the Modern Enterprise℠
The future of business is being driven by cloud computing, virtual workforces, and dynamic collaboration technologies. This rapidly evolving environment makes data protection and cybersecurity… Read More »Edgile Overview – We Secure the Modern Enterprise℠
Healthcare CISO Accelerators
Preventative Cybercare is Good Medicine for Your Security Program. Today’s cyber attacks can be inside networks for well over 200 days before they are detected.… Read More »Healthcare CISO Accelerators
Modernize identity governance with cloud-hosted managed services
As IT environments become increasingly complex, many organization lack the expertise to migrate workloads to the cloud and manage cloud programs at scale. Edgile offers… Read More »Modernize identity governance with cloud-hosted managed services
The importance of Identity and Access as enterprises shift to the cloud
Business operations are becoming more complex as the number and type of users increases, coupled with their ability to access a growing diversity of IT… Read More »The importance of Identity and Access as enterprises shift to the cloud
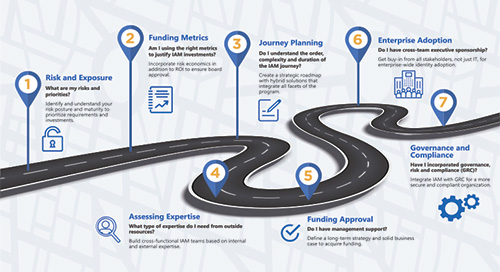
7 Key Considerations on the Road to High-Performing IAM
Are you asking the right IAM questions? Follow our infographic to start your journey. As you continue to purchase and implement IAM technology these seven… Read More »7 Key Considerations on the Road to High-Performing IAM
Why Leading CISOs are Adopting a Strategy-First Approach to IAM
Learn how your company should benefit from a multi-perspective IAM plan. With mounting security threats and audit and regulatory deadlines, CISOs are challenged with the… Read More »Why Leading CISOs are Adopting a Strategy-First Approach to IAM